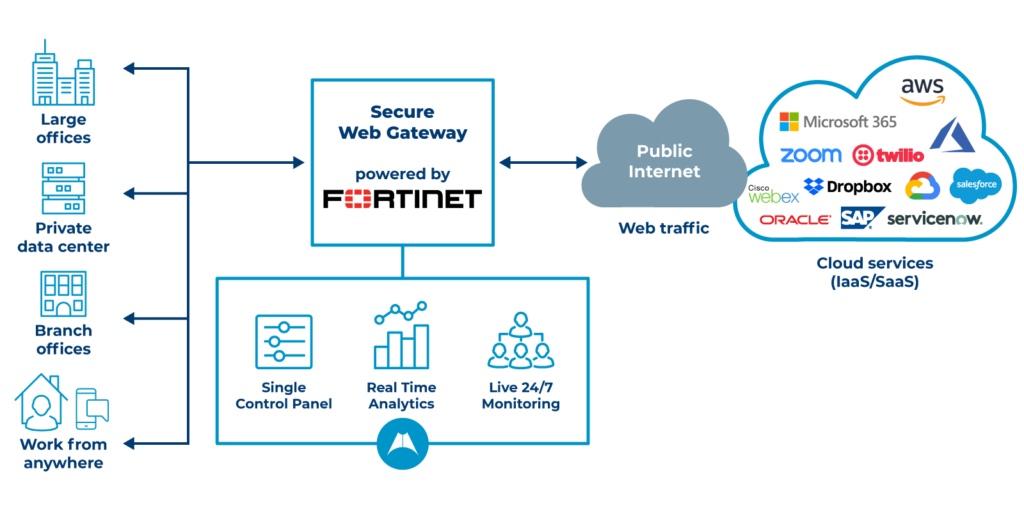
Secure Web Gateway (SWG)
Secure Web Gateway (SWG) protects organizations across the web, social media, applications, and mobile networks to safeguard organizations from online threats. SWG acts as a proxy between users and the internet to identify malicious websites and payloads and to control access to sensitive content
The Challenge
Data breaches, malware attacks, and other deadly cyberthreats are posing greater risks to businesses and consumers alike.
As enterprises and their mobile workforces grow, it becomes increasingly difficult to protect mobile users from threats. This is because organizations have a variety of applications, some located at headquarters and some in the cloud.
Applications at headquarters are accessed through a remote access VPN. When users access cloud applications, they are disconnected from the VPN and exposed to risk.
The Solution
A Secure Web Gateway (SWG) is a cybersecurity solution that protects systems and data and helps enforce security policies in a company. SWG provides secure internet access when users are disconnected from the VPN.
SWG
Zero Trust
Treating all content as if it is malicious eliminates the need to make an allow-or-block decision at the point of click. Zero Trust ensures that all traffic is secured and nothing can slip through the cracks.
What is a secure web gateway?
A secure web gateway is a security solution that prevents unsecured traffic from entering an internal network of an organization. It is used by enterprises to protect their employees and users from accessing and being infected by malicious Web traffic, websites, viruses and malware. It also ensures the implementation and compliance of the organization’s regulatory policy.
Secure Web Gateways can be either on-premises or cloud-delivered and are located between users and the internet, blocking malicious applications, and preventing access to websites that are known to be bad. In this manner, unsecured traffic is prevented from gaining network access, protecting users from infection by malicious traffic, websites, viruses, and other malware. In addition, a secure web gateway ensures compliance with an organization’s regulatory policies and frameworks.
SWGs are expected to have the following minimum set of functionality:
- URL filtering
- Malicious-code detection and filtering
- Application controls for popular web-based apps such as Skype and Zoom
- Native or integrated data loss prevention
What Are The Capabilities of Secure Web Gateway (SWG)?
A secure web gateway (SWG) protects users from web-based threats in addition to applying and enforcing corporate acceptable use policies. Instead of connecting directly to a website, a user accesses the SWG, which is then responsible for connecting the user to the desired website and performing functions such as URL filtering, web visibility, malicious content inspection, web access controls and other security measures.
SWGs enable companies to:
- Block access to inappropriate websites or content based on acceptable use policies
- Enforce their security policies to make internet access safer
- Help protect data against unauthorized transfer
Secure Web Gateway vs. Firewall
SWGs prevent malware infections, block access to malicious websites and applications, and enforce company compliance policies, especially at branch offices and for remote workers.
SWGs are similar to firewalls in that they both can discern malicious Internet traffic from benign traffic, and both provide advanced network security protections. Firewalls function at the packet level. The primary role of SWGs, however, is to identify and protect against advanced attacks by inspecting web traffic at the application level—without compromising on overall web experience.
A fully integrated enterprise security strategy requires both SWGs and next-generation firewalls (NGFW).
Why is a secure web gateway important?
Secure web gateways have become increasingly common as cybercriminals have grown more sophisticated in embedding threat vectors into seemingly innocuous or professional-looking websites. These counterfeit websites can compromise the enterprise as users access them, unleashing malicious code and unauthorized access in the background without the user’s knowledge. The fake, criminal websites can be quite convincing.
Some of these scam websites appear to be so authentic that they can convince users to enter credit card numbers and personal identification information (PII) such as social security numbers. Other sites require only the connection to the user to bypass web browser controls and inject malicious code such as viruses or malware into the user’s network. Examples include fake online shopping sites posing as brand-name sellers, sites that appear to be legitimate government agencies, and even business-to-business intranets. Secure web gateways can also prevent data from flowing out of an organization, making certain that restricted data is blocked from leaving the organization.
How Does a Secure Web Gateway Work?
Secure web gateways are installed as a software component or a hardware device on the edge of the network or at user endpoints. All traffic to and from users to other networks must pass through the gateway that monitors it. The gateway monitors this traffic for malicious code, web application use, and all user/non-user attempted URL connections.
The gateway checks or filters website URL addresses against stored lists of known and approved websites—all others not on the approved lists can be explicitly blocked. Known malicious sites can be explicitly blocked as well. URL filters that maintain allowed web addresses are maintained in whitelists, while known, off-limits sites that are explicitly blocked are maintained in blacklists. In enterprises, these lists are maintained in the secure gateway’s database, which then applies the list filters to all incoming and outgoing traffic.
Similarly, data flowing out of the network can be checked, disallowing restricted data sources—data on the network or user devices that is prohibited from distribution. Application level controls can also be restricted to known and approved functions, such as blocking uploads to software-as-a-service (SaaS) applications (such as Office 365 and Salesforce.com). Although some enterprises deploy secure web gateways in hardware appliances that filter all incoming and outgoing traffic, many organizations use cloud-based, software-as-a-service (SaaS) secure web gateways as a more flexible and less costly solution to deploy and maintain. Organizations with existing hardware investments often combine the two, using hardware at their larger physical sites and cloud-based gateways for remote locations and travelling workers.
How Do You Implement a Secure Web Gateway?
As with most infrastructure, secure web gateways can be deployed on-premises, in the cloud, or in a hybrid fashion. All of these deployments support in-line connection which sends all web traffic to the SWG via proxy, client-based agents, or other routing method.
As a rule, SWGs are deployed as a workload running on a server, whether physical or virtual machine. Some SWGs are available as appliances. The largest growth is on the cloud-based SWG market.