Network Detection and Response (NDR)
Network detection and response (NDR) is a real-time, automated threat detection and response solution for advanced cyber security attacks. The rise of NDR systems reflects the growing number of systemwide attacks by criminal actors ranging from hackers to nation-states.
NDR
Automatically
respond and shut down attacks in real-time with Network Detection and Response (NDR)
NDR solution provides a comprehensive view into all enterprise devices, entities, and network traffic. NDR monitors and analyzes all traffic flows in real time and monitor and analyze not only traffic that enters and exits the environment, but also all traffic that moves laterally across the network.
What is Network Detection and Response (NDR)?
Network detection and response (NDR) is a cybersecurity solution that continuously monitors an organization’s network to detect cyber threats & anomalous behavior using non-signature-based tools or techniques and responds to these threats via native capabilities or by integrating with other cybersecurity tools/solutions.
How does NDR work?
NDR solutions continuously monitor and analyze raw enterprise network traffic to generate a baseline of normal network behavior. When suspicious network traffic patterns that deviate from this baseline are detected, NDR tools alert security teams to the potential presence of threats within their environment.
Highly performant NDR solutions use advanced machine learning and artificial intelligence tools to model adversary tactics, techniques and procedures that are mapped in the MITRE ATT&CK framework to detect attacker behaviors with high precision.
What does distinguish NDR?
While attackers may be able to fool firewalls and traditional IDS by masquerading as legitimate users and services and avoiding signature-based detection, they can’t escape NDR. That is because it is almost impossible for them to avoid certain key activities on the network, which NDR can detect.
What are the benefits of implementing the NDR?
What is the difference between the firewall and NDR?
Firewalls are often described as the first line of defense against malicious attacks on a network. They operate at the perimeter of a network and block potentially dangerous traffic. Sometimes they are compared to security gates.
An NDR system operates differently from this kind of security system. It can be compared to a security camera, monitoring for intruders who slip through the gates and lurk within the network. An NDR also analyzes potential problems and initiates a network response to address any damage caused to the network.
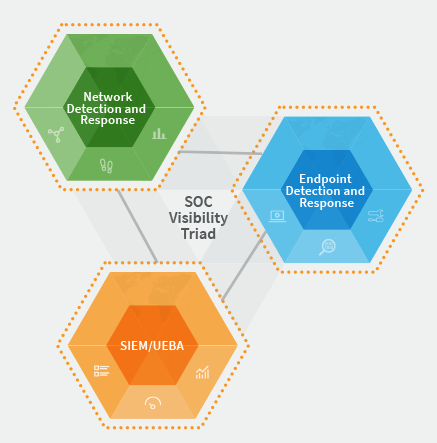
SOC
Gartner SOC visibility
triad & Network Detection and Response (NDR)
NDR plays a pivotal role in securing your digital infrastructure. Threat history is generally available in three places: network, endpoint and logs.
OFFERINGS
Vectra® is an artificial intelligence company that is transforming cybersecurity. Its Cognito™ platform is the fastest, most efficient way to detect and respond to cyberattacks, reducing security operations workload by 168X. Cognito performs real-time attack hunting by analyzing rich metadata from network traffic, relevant logs and cloud events to detect attacker behaviors within all cloud and data center workloads, and user and IoT devices.





