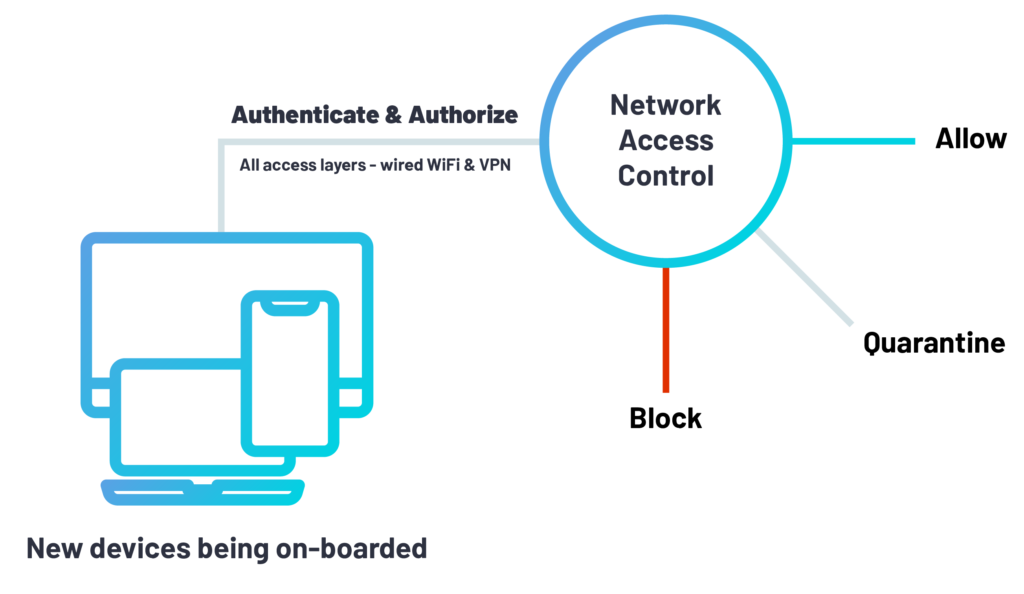
Network Access Control (NAC)
Network access control (NAC), also known as network admission control ensures that only users who are authenticated and devices that are authorized and compliant with security policies can enter the network.
The Challenge
An organization must keep out the unauthorized users include cybercriminals, hackers and data thieves, and other bad actors trying to access the network. But businesses must also be gatekeepers for authorized users. This particularly applies to organizations that allow remote access to the enterprise network from non-corporate devices like mobile phones, laptops and tablets, or companies that allow employees working in the office to use personal devices. Both scenarios create security risks demanding organizations to address network security.
The Solution
Network access control (NAC) provides the visibility, access control, and compliance capabilities that are required to strengthen your network security infrastructure.
A NAC system can deny network access to noncompliant devices, place them in a quarantined area, or give them only restricted access to computing resources, thus keeping insecure nodes from infecting the network.
NAC
Add A Layer
of Security to The Network
NAC plays a key role in maintaining access privileges while ensuring guest users have smooth connectivity and a good overall experience.
What Is Network Access Control?
Network access control (NAC) is a security software that businesses can use to control the amount and level of access to their networks.
There are many NAC tools available, and the functions are often performed by a network access server. Effective network access control restricts access to only those devices that are authorized and compliant with security policies, meaning they have all the required security patches and anti-intrusion software. Network operators define the security policies that decide which devices or applications comply with endpoint security requirements and will be allowed network access.
Essentially, NAC is intended to address two issues:
- Authentication: Only authorized devices should be granted access to the network, such as an employee’s personal laptop. In contrast, a hacker’s harmful devices should be blocked from the network.
- Compliance: Authenticated devices are granted authorization when they meet additional criteria. These include passing tests for current antivirus patterns and OS patch level requirements.
How Network Access Control Secures Your Network?
NAC network security provides visibility over everything connected to the network, as well as the ability to control those devices and users, including dynamic, automated responses. It plays a role in strengthening overall network security infrastructure.
A properly functioning solution can prevent access to noncompliant users or devices, place them in quarantine, or restrict access to a small number of network resources, separated from the rest of the network. A network access control policy generally supports the following:
- Authentication and authorization of users and devices
- User and device profiling
- Denial of unsecured devices
- Quarantine of unsecured devices
- Restricting access to unsecured devices
- Policy lifecycle management
- Overall security posture assessment
- Incident response through policy enforcement
- Guest networking access
What Is The Importance of Network Access Control?
NAC is critical for modern businesses because it allows organizations to monitor the devices and users — authorized and unauthorized — trying to access the network.
Unauthorized users include cybercriminals, hackers and data thieves, and other bad actors that an organization must keep out. But businesses must also be gatekeepers for authorized users. This particularly applies to organizations that allow remote access to the enterprise network from non-corporate devices like mobile phones, laptops and tablets, or companies that allow employees working in the office to use personal devices. Both scenarios create security risks demanding organizations to address network security.
NAC is one aspect of network security. It provides visibility into the devices and users trying to access the enterprise network. And it controls who can access the network, including denying access to those users and devices that don’t comply with security policies. NAC solutions and tools help companies control network access, ensure compliance and strengthen their IT infrastructure.
NAC Capabilities
NAC excels at addressing several traditional types of security needs:
- Conventional network visibility: NAC can help identify which devices exist on your network, who has access to them and how they can share resources with each other.
- Endpoint security technology: NAC helps ensure that network endpoints—meaning physical or virtual resources that can send or receive data over the network—are secured against known vulnerabilities.
- Authentication: NAC policies ensure that users and devices authenticate properly before they are allowed to use a network by, for example, preventing a computer from joining a wireless network unless its user enters the right passphrase.
- Network security enforcement: NAC can identify instances where devices are not compliant with authentication or security policies.
What Is The Network Access Server?
Many NAC functions are performed by a network access server. A traditional network access server is a server that performs authentication and authorization functions by verifying user logon information. Also known as a media access gateway or remote access server, a network access server handles remote logins, establishes point-to-point protocol connections and ensures that authorized users can access the resources they need.
A network access server can function in several ways, such as the following:
- Internet service provider: enables authorized customers to access the internet.
- Virtual private network (VPN): gives remote users access to a private enterprise network and resources.
- Voice over Internet Protocol: allows users to access communication applications over the internet.
A network access server can also support the following:
- Network load balancing to distribute traffic and improve reliability and performance;
- Network resource management to manage and allocate resources for networking processes; and
- Network user sessions to track users, store their data and persist their specific state.
What Are Common Use Cases For Network Access Control?
If an organization’s security policy allows any of the following circumstances, they need to think carefully about network access control to ensure enterprise security:
- Bring Your Own Device (BYOD): Any organization that allows employees to use their own devices or take corporate devices home needs to think beyond the firewall to ensure network security. Each device creates a vulnerability that could make it possible for cyber criminals to get around traditional security controls.
- Network access for non-employees: Some organizations need to grant access to people or devices that are outside of the organization and not subject to the same security controls. Vendors, visitors, and contractors may all need access to the corporate network from time to time, but not to all parts of the network and not every day.
- Use of IoT devices: The Internet of Things has given rise to a proliferation of devices that may fly under the radar of traditional security controls, often residing outside of the physical corporate building, but still connected to the corporate network. Cyber criminals can easily exploit these overlooked devices to find their way into the heart of the network without adequate network access controls. Network access control is an important aspect of edge security solutions.
- NAC for medical devices: Medical devices that collect data about patients or, in some cases, are implanted inside them, can be used as gateways to collect sensitive data, such as protected health information or financial systems. NAC can mitigate these threats by segmenting medical devices from the rest of the network in order to minimize the attack surface. It can also ensure that medical devices are connected only when necessary, which also helps to minimize opportunity for attack.
- Incident Response: The role of NAC in incident response is often significant. Network access control solutions can be configured to automatically enforce security policies, share contextual information, and isolate unsecure devices from accessing other parts of a network.
How Does Network Access Control Work?
To understand how NAC can help, we first must understand how it works.
The license of the NAC solution that you bought would be uploaded on to either a physical server or a virtual machine.
However, you will need a professional certified in the implementation of that product to get things rolling—NAC isn’t something that you can just download and carry out yourself.
Then, network access control works by utilizing your Active Directory (or other directory system/multi-authentication platforms) and allows you to create a list of rules—or policies— that it enforces on each device that attempts access to your network.
That way you can provide different levels of access to the network based on who you are and what you need.
For example, if you work at a college and you’re a network admin, you would have the most access to the network, while a CMO would have less access but still more than a college student, and a college student would have more access than a guest to the network.
Think of NAC as your guard and your network is the club that everyone wants to get into. The guard is looking at your ID, making sure that you’re on the list, seeing if your outfit adheres to the dress code, etc. Then, depending on your level of celebrity status, determines what level of the club you’re allowed to go to—all the way up to the VIP lounge.
This is a valuable solution for businesses who have a lot of people wanting to get into their “Club Network”.