Email Security
Email Security provides everything you need to protect against cyber attacks and phishing, secure business continuity, and ensure email compliance
The Challenge
Email attacks are getting more complex and dangerous. Email is often used to spread malware, spam and phishing attacks. Attackers use deceptive messages to entice recipients to part with sensitive information, open attachments or click on hyperlinks that install malware on the victim’s device.
Social actions such as phishing and email scams arrive via email 96% of the time, and these security threats are always evolving.
The Solution
Email Protection provides the most comprehensive protection against all email threat types, from spam and ransomware to socially engineered threats such as spear phishing, business email compromise, and account takeover.
Email Protection
Detect and block
advanced malware by email security
Our email security solutions detect email with malicious URLs or attachments. And block ransomware and polymorphic malware. Re-writing URLs protects your users on any network and device.
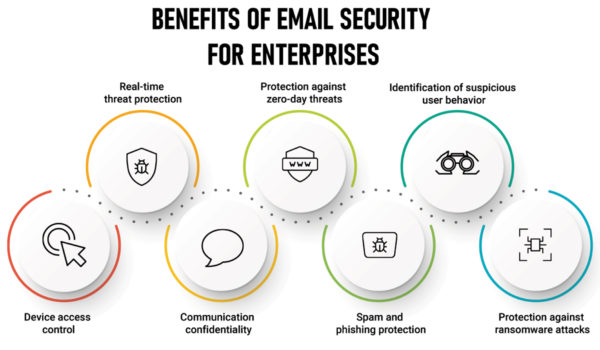
What Is Email Security?
Email security includes the techniques and technologies used to protect email accounts and communications. Email security is important because email contains sensitive information, is used by everyone in the organization, and is therefore one of a company’s largest targets for attacks. The shift to cloud-based email like Gmail and others comes with several benefits, but cloud-based email has become a tempting attack surface for cyber criminals.
Why Email Security is Important?
It’s important that users and organizations take measures to guarantee the security of their email accounts against known attacks, and it’s especially important that a proper infrastructure is in place to stop any unauthorized attempts at accessing accounts or communications. Users are especially susceptible to phishing attacks against businesses, because they sidestep technical security protections, and instead lean into users themselves to expose weaknesses. This is why email security solutions should start with proper techniques like encryption, spyware detection, and login security. But it’s equally important that employees are educated on the proper steps that should be taken to protect email.
What are the types of email attacks?
Cyber criminals use many different tactics to hack email, and some methods can cause considerable damage to an organization’s data and/or reputation. Malware, which is malicious software used to harm or manipulate a device or its data, can be placed on a computer using each of the following attacks.
- Phishing
A phishing attack targets users by sending them a text, direct message, or email. The attacker pretends to be a trusted individual or institution and then uses their relationship with the target to steal sensitive data like account numbers, credit card details, or login information.
Phishing comes in several forms, such as spear phishing, regular phishing, and whaling. Spear phishing targets a particular person, while a whaler targets someone high up in the organization by pretending to be someone they trust. - Spam:
Often, spam email is sent for commercial purposes. While some people view it as unethical, many businesses still use spam. The cost per email is incredibly low, and businesses can send out mass quantities consistently. Spam email can also be a malicious attempt to gain access to your computer.
Spam email can be dangerous. It can include malicious links that can infect your computer with malware . Do not click links in spam. Dangerous spam emails often sound urgent, so you feel the need to act. Keep reading to learn about some of the basic spam types. - Spoofing:
Spoofing is a dangerous email threat because it involves fooling the recipient into thinking the email is coming from someone other than the apparent sender. This makes spoofing an effective business email compromise (BEC) tool. The email platform cannot tell a faked email from a real one because it merely reads the metadata—the same data the attacker has changed.
This makes the impersonation of a person the victim either knows or respects relatively easy for an attacker.
What are the best practices for email security?
Email is a primary weapon for spreading ransomware, an advanced threat that can affect multiple endpoints as well as steal sensitive data. Therefore, an email protection plan needs to include the following best practices to protect email traffic in real time.
- Spam filter: A spam filter can detect spam and keep it from either hitting your inbox or file it as junk mail.
- Email encryption: Email encryption can disguise corporate email by changing communications into a garbled arrangement of letters, numbers, and symbols that someone who intercepts it cannot read.
- Antivirus protection: Antivirus protection screens emails and attachments for viruses, providing the user with warnings if anything suspicious is detected.
- Secure email gateway (SEG): An SEG filters out potentially dangerous emails according to the settings of an IT administrator.
- Multi-factor authentication (MFA): MFA is a key data loss protection and anti-hacking tool because it requires a user to provide more than one authentication factor to prove they should be granted access to a system.
- Employee Awareness: Employees can be educated to recognize social engineering, phishing, and other types of attacks that are typically executed using email.