Data Loss Prevention (DLP)
Data loss prevention (DLP) enables businesses to detect data loss, as well as prevent the illicit transfer of data outside the organization and the unwanted destruction of sensitive or personally identifiable data
The Challenge
Data loss occurs when confidential or private information leaves the enterprise as a result of unauthorized communication through channels such as applications, physical devices, or network protocols.
The Solution
DLP provides comprehensive protection for all potential leaking channels, including removable storage devices, the cloud, email, instant messaging, web, printing, clipboard, screenshot, and file-sharing applications.
DLP
Data Loss Prevention
Focuses on Real Security and Compliance
DLP products use business rules to classify and protect confidential and critical information so that unauthorized users cannot accidentally or maliciously share data, which would put the organization at risk
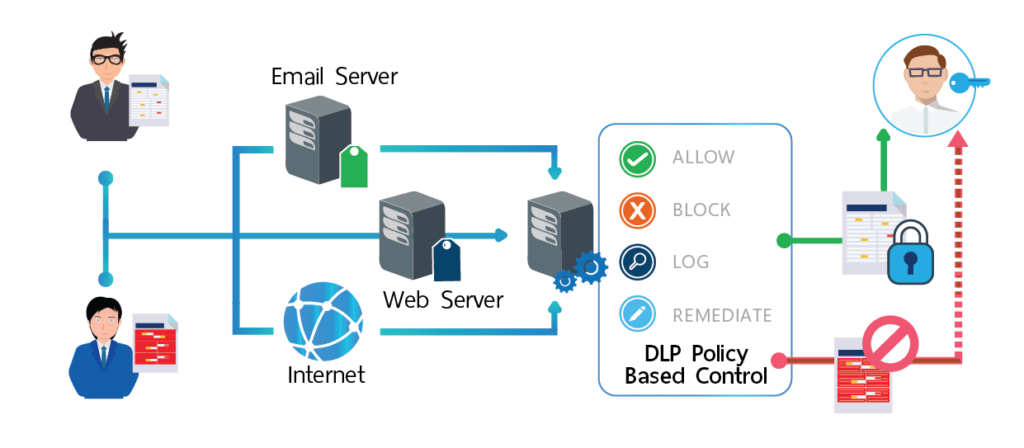
How DLP works?
DLP systems protect businesses’ data by identifying sensitive information, then using deep content analysis to detect and prevent potential data leaks. This content analysis uses methods like keyword matches, regular expressions, and internal functions to recognize content that matches a company’s DLP policy. As a result, businesses can identify, monitor, and automatically prevent the theft or exposure of protected data.
In a short, DLP identifies sensitive data or user activity, takes action on policy violations, and creates incidents of violations.
Data Loss Prevention (DLP) Features
Data Loss Prevention (DLP) Benefits
- Prevents inadvertent releases of sensitive business information to connections, e.g. on social media sites
- Provides assurances of a comprehensive organization-wide data management
- Complies with legal or standard requirements, including SOX or HIPAA on data confidentiality. The DLP solution enables organizations to maintain the compliance
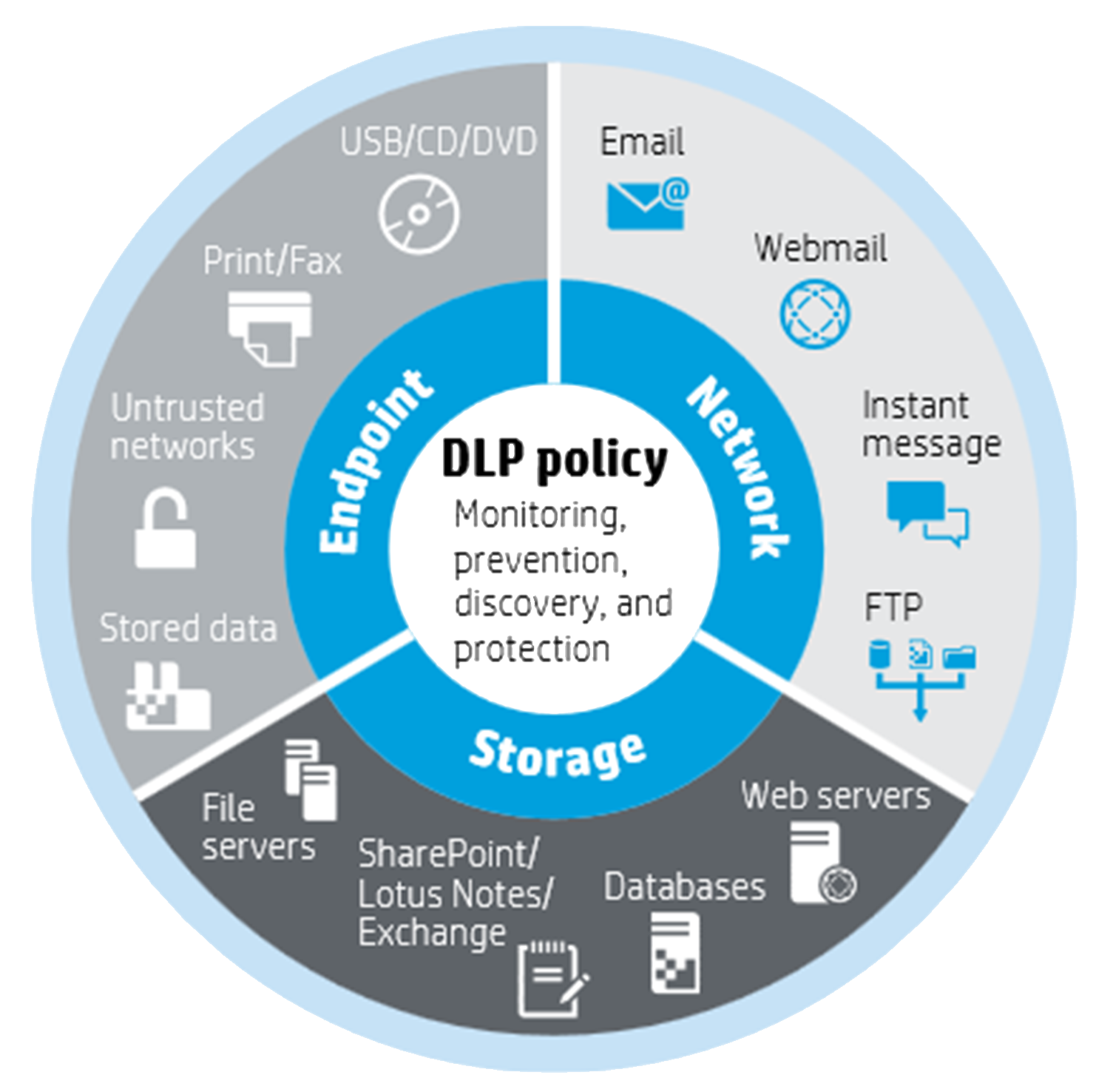
Data Loss Prevention: Safeguard Important Data
Data Loss Prevention (DLP) safeguards important data, including financial information, customer contacts, contracts, etc. without interfering with normal operations. Once a potential leakage takes place, the system would immediately inspect and intercept the relevant act. This helps reduce unauthorized transmission of data and thereby minimize damages to the organization.




